
Relution Shield
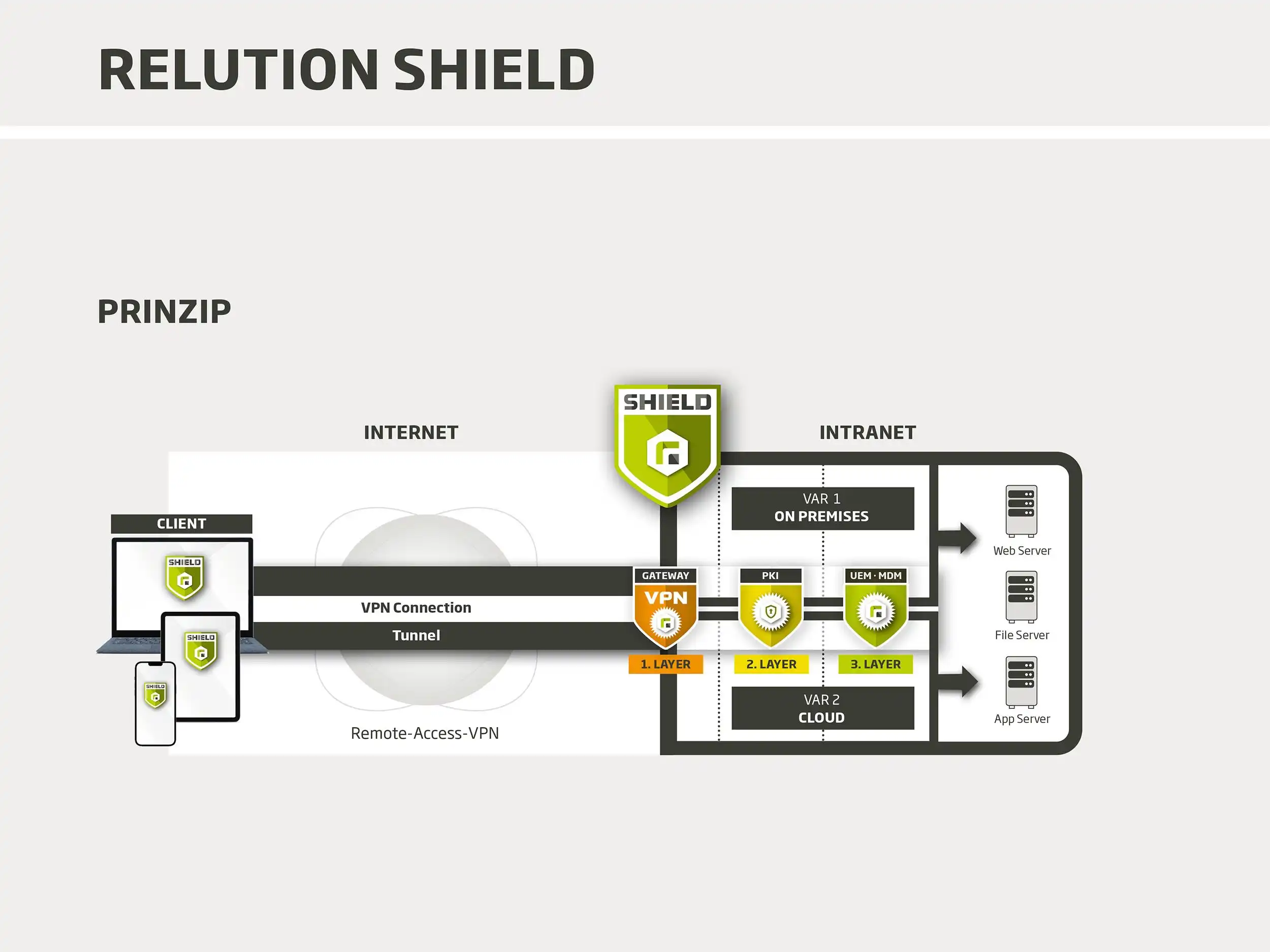
Relution Shield combines Virtual Private Network (VPN), Public Key Infrastructure (PKI) and UEM · MDM.
For organizational communication, this means triple-secured access from and to the outside.
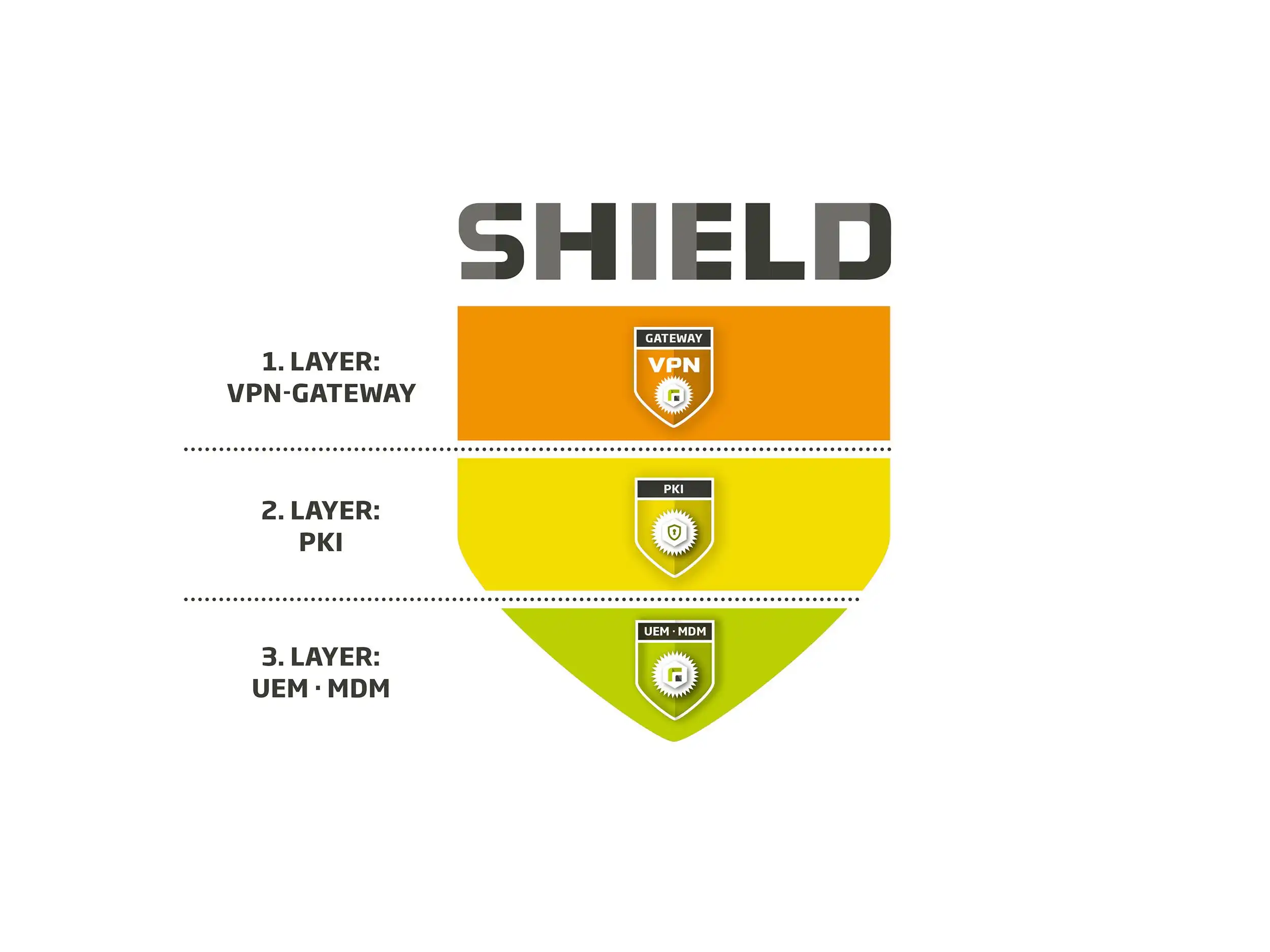
1st security layer:
VPN gateway
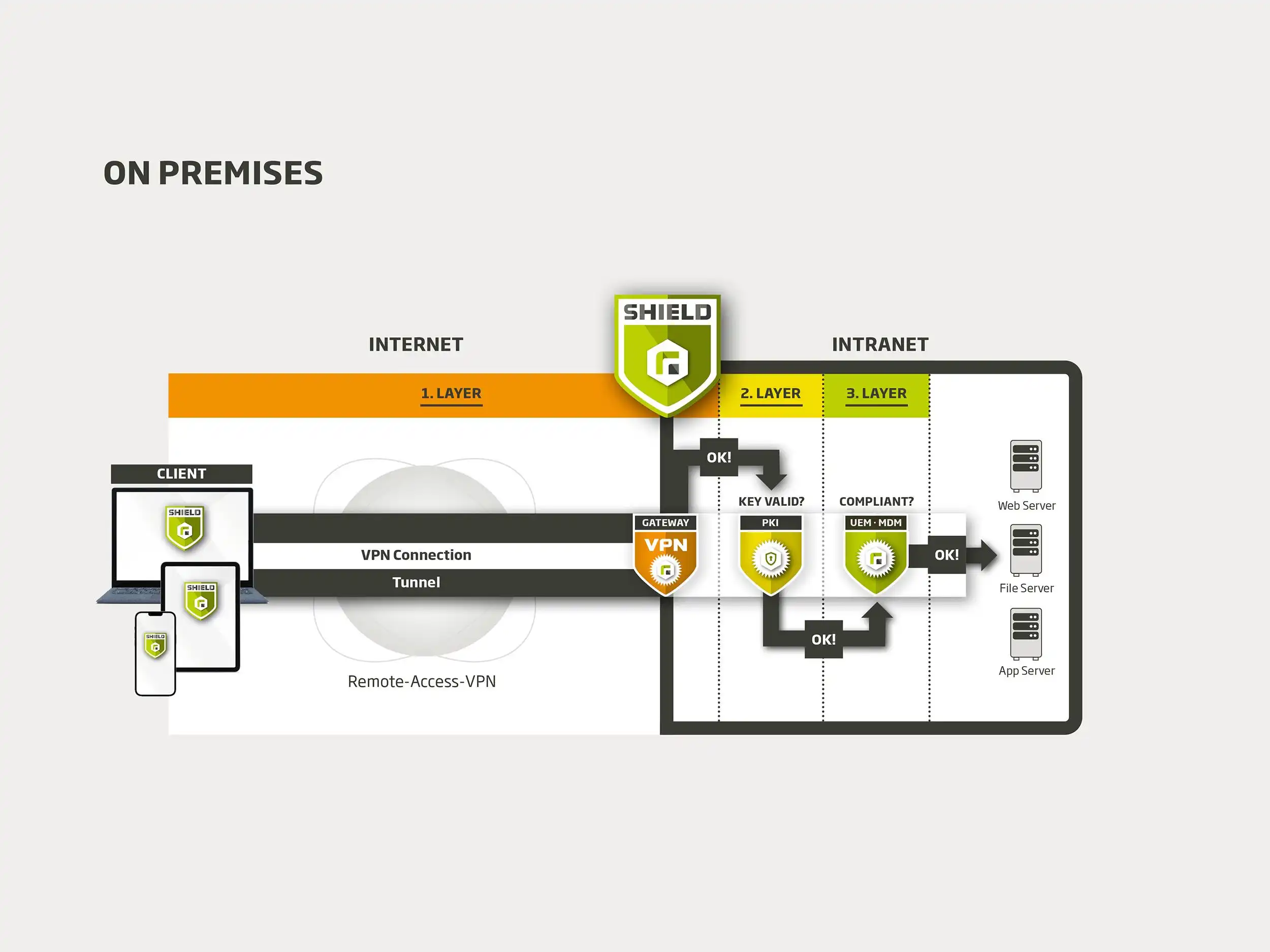
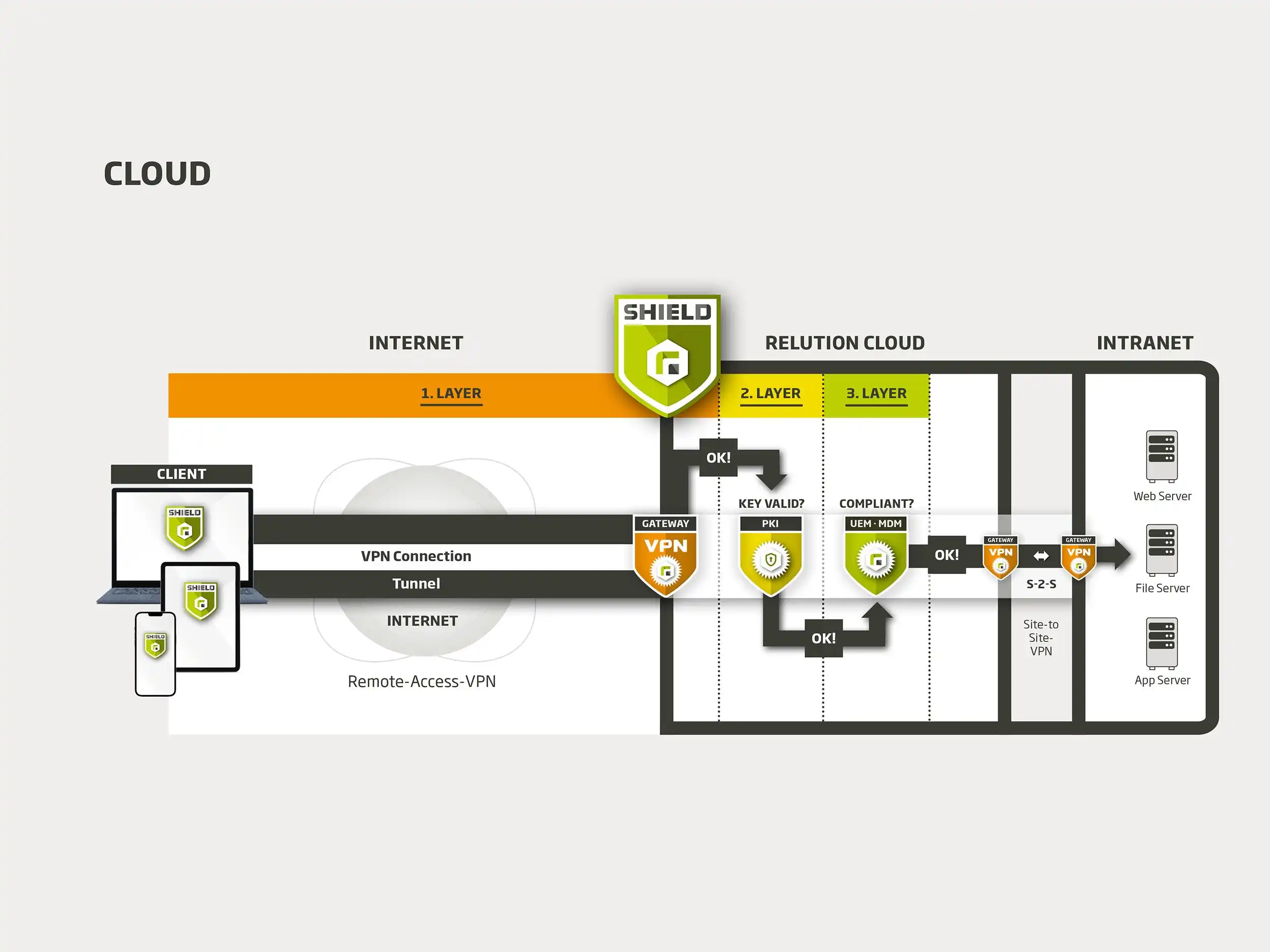
A Virtual Private Network, or VPN for short, is a virtual network: A VPN connection establishes a secure connection between the devices used and the Intranet. In this way, data traffic is encrypted via the VPN. With a VPN, the end devices are not directly physically connected to each other or to a central router - for example via network cables or a WiFi connection - but use the public Internet as a transmission path. All data transmitted between the end device and the VPN gateway is encrypted to isolate it from the rest of the Internet.
The encrypted data line is also known as a "VPN tunnel", as it creates a tap-proof "tunnel" through the Internet. To allow an external end device to access an organizational intranet, security software on the end device - the "client" - is used to create a tunnel to the organization's VPN server. Information is broken down into "data packets" and reassembled into the original format at the recipient's end. The VPN gateway is the "doorkeeper" and only opens access if certain security parameters are met.
2nd security layer:
PKI
From a security point of view, a VPN connection is one of the strongest encryption options. However, the weak point lies in the use of static passwords. As a solution, Relution Shield offers a built-in Public Key Infrastructure (PKI) that uses certificates instead of passwords to authenticate users. The Relution "Built-In PKI" sends a certificate with keys to each enrolled device in advance. When an attempt is made to access the intranet via the VPN tunnel, the virtual ID is automatically checked. The VPN tunnel is only established once the authentication has been verified.
3. security layer:
UEM · MDM
Relution is a market-leading unified endpoint management (UEM) and mobile device management (MDM) software that works in accordance with GDPR guidelines and is used in both the public and private sectors. The profiles in the software define the security guidelines to secure issued and enrolled devices against misuse. Relution Shield also checks whether devices are trustworthy and do not violate company guidelines.
Tech Facts
- VPN infrastructure
- Relution Built-In PKI
- Extension: Relution Compliance Check
- VPN Profile IKEv2
- On Demand Rules for iOS, macOS & Android
- Per App / Profile VPN
- Always on VPN
- Available as Relution AddOn.
Photos: MWAY, istockphoto (Prykhodov)